Follow the steps below to load the driver JAR in DBeaver. Open the DBeaver application and, in the Databases menu, select the Driver Manager option. Click New to open the Create New Driver form. Cosmos DB You will compare the different APIs available in Azure Cosmos DB, highlighting and contrasting the different scenarios that would make them a good choice for a company. Azure Cosmos DB Conf - Microsoft 29 March 2021, Channel 9. Azure SDK Gets Communications Services Libraries, Based on Teams Tech 22 April 2021, Visual Studio Magazine. NoSQL Software Market Information, Figures and Analytical Insights 2021– 2026 MongoDB, OrientDB, Amazon, Azure Cosmos DB 9 April 2021, The Courier. ) But, you also need to think about integrating with other systems with existing data and bringing that into Azure Cosmos DB. DBeaver uses DataStax Java driver 3. If you are trying to do that you could get an exception containing something likeThe driver is compatible with Apache Cassandra® 2. May 12, 2020 Note: Make sure to.
-->APPLIES TO: SQL API Cassandra API Gremlin API Table API Azure Cosmos DB API for MongoDB
Note
This article is about role-based access control for management plane operations in Azure Cosmos DB. If you are using data plane operations, see Azure Cosmos DB RBAC for role-based access control applied to your data plane operations.
Dbeaver Cosmos Db Connect
Azure Cosmos DB provides built-in Azure role-based access control (Azure RBAC) for common management scenarios in Azure Cosmos DB. An individual who has a profile in Azure Active Directory can assign these Azure roles to users, groups, service principals, or managed identities to grant or deny access to resources and operations on Azure Cosmos DB resources. Role assignments are scoped to control-plane access only, which includes access to Azure Cosmos accounts, databases, containers, and offers (throughput).
Built-in roles
The following are the built-in roles supported by Azure Cosmos DB:
| Built-in role | Description |
|---|---|
| DocumentDB Account Contributor | Can manage Azure Cosmos DB accounts. |
| Cosmos DB Account Reader | Can read Azure Cosmos DB account data. |
| Cosmos Backup Operator | Can submit a restore request for Azure portal for a periodic backup enabled database or a container. Can modify the backup interval and retention on the Azure portal. Cannot access any data or use Data Explorer. |
| CosmosRestoreOperator | Can perform restore action for Azure Cosmos DB account with continuous backup mode. |
| Cosmos DB Operator | Can provision Azure Cosmos accounts, databases, and containers. Cannot access any data or use Data Explorer. |
Important
Azure RBAC support in Azure Cosmos DB applies to control plane operations only. Data plane operations are secured using primary keys or resource tokens. To learn more, see Secure access to data in Azure Cosmos DB
Identity and access management (IAM)
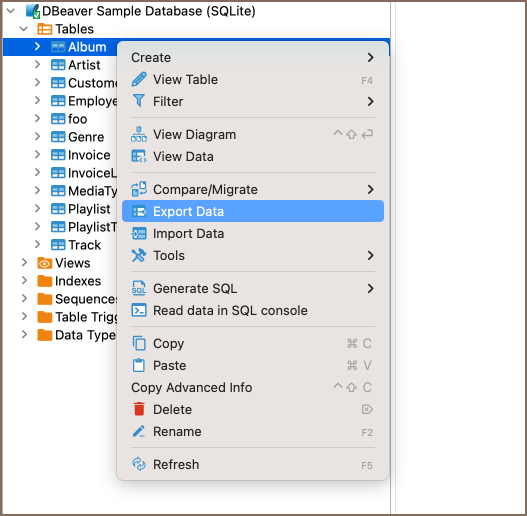
The Access control (IAM) pane in the Azure portal is used to configure Azure role-based access control on Azure Cosmos resources. The roles are applied to users, groups, service principals, and managed identities in Active Directory. You can use built-in roles or custom roles for individuals and groups. The following screenshot shows Active Directory integration (Azure RBAC) using access control (IAM) in the Azure portal:
Custom roles
Dbeaver Cosmos Db Download

In addition to the built-in roles, users may also create custom roles in Azure and apply these roles to service principals across all subscriptions within their Active Directory tenant. Custom roles provide users a way to create Azure role definitions with a custom set of resource provider operations. To learn which operations are available for building custom roles for Azure Cosmos DB see, Azure Cosmos DB resource provider operations
Tip
Custom roles that need to access data stored within Cosmos DB or use Data Explorer in the Azure portal must have Microsoft.DocumentDB/databaseAccounts/listKeys/* action.
Preventing changes from the Azure Cosmos DB SDKs
The Azure Cosmos DB resource provider can be locked down to prevent any changes to resources from a client connecting using the account keys (that is applications connecting via the Azure Cosmos SDK). This also includes changes made from the Azure portal. This feature may be desirable for users who want higher degrees of control and governance for production environments. Preventing changes from the SDK also enables features such as resource locks and diagnostic logs for control plane operations. The clients connecting from Azure Cosmos DB SDK will be prevented from changing any property for the Azure Cosmos accounts, databases, containers, and throughput. The operations involving reading and writing data to Cosmos containers themselves are not impacted.
When this feature is enabled, changes to any resource can only be made from a user with the right Azure role and Azure Active Directory credentials including Managed Service Identities.

The Access control (IAM) pane in the Azure portal is used to configure Azure role-based access control on Azure Cosmos resources. The roles are applied to users, groups, service principals, and managed identities in Active Directory. You can use built-in roles or custom roles for individuals and groups. The following screenshot shows Active Directory integration (Azure RBAC) using access control (IAM) in the Azure portal:
Custom roles
Dbeaver Cosmos Db Download
In addition to the built-in roles, users may also create custom roles in Azure and apply these roles to service principals across all subscriptions within their Active Directory tenant. Custom roles provide users a way to create Azure role definitions with a custom set of resource provider operations. To learn which operations are available for building custom roles for Azure Cosmos DB see, Azure Cosmos DB resource provider operations
Tip
Custom roles that need to access data stored within Cosmos DB or use Data Explorer in the Azure portal must have Microsoft.DocumentDB/databaseAccounts/listKeys/* action.
Preventing changes from the Azure Cosmos DB SDKs
The Azure Cosmos DB resource provider can be locked down to prevent any changes to resources from a client connecting using the account keys (that is applications connecting via the Azure Cosmos SDK). This also includes changes made from the Azure portal. This feature may be desirable for users who want higher degrees of control and governance for production environments. Preventing changes from the SDK also enables features such as resource locks and diagnostic logs for control plane operations. The clients connecting from Azure Cosmos DB SDK will be prevented from changing any property for the Azure Cosmos accounts, databases, containers, and throughput. The operations involving reading and writing data to Cosmos containers themselves are not impacted.
When this feature is enabled, changes to any resource can only be made from a user with the right Azure role and Azure Active Directory credentials including Managed Service Identities.
Warning
Enabling this feature can have impact on your application. Make sure that you understand the impact before enabling it.
Check list before enabling
This setting will prevent any changes to any Cosmos resource from any client connecting using account keys including any Cosmos DB SDK, any tools that connect via account keys, or from the Azure portal. To prevent issues or errors from applications after enabling this feature, check if applications or Azure portal users perform any of the following actions before enabling this feature, including:
Any change to the Cosmos account including any properties or adding or removing regions.
Creating, deleting child resources such as databases and containers. This includes resources for other APIs such as Cassandra, MongoDB, Gremlin, and table resources.
Updating throughput on database or container level resources.
Modifying container properties including index policy, TTL and unique keys.
Modifying stored procedures, triggers or user-defined functions.
If your applications (or users via Azure portal) perform any of these actions they will need to be migrated to execute via ARM Templates, PowerShell, Azure CLI, REST, or Azure Management Library. Note that Azure Management is available in multiple languages.
Set via ARM Template
To set this property using an ARM template, update your existing template or export a new template for your current deployment, then include the 'disableKeyBasedMetadataWriteAccess': true to the properties for the databaseAccounts resources. Below is a basic example of an Azure Resource Manager template with this property setting.
Important
Make sure you include the other properties for your account and child resources when redploying with this property. Do not deploy this template as is or it will reset all of your account properties.
Set via Azure CLI
To enable using Azure CLI, use the command below:
Set via PowerShell
To enable using Azure PowerShell, use the command below: